Cyber Smart Parents & Educators
- MOULDING A CYBER SMART GENERATION
- AN INSIGHT INTO REALITY
- ONLINE GENERATION GAP
- CYBER BULLYING & HARASSMENT
- INTERNET SAFETY TIPS FOR PARENTS
- THE FAMILY Internet SAFETY CONTRACT
- SOFTWARE PIRACY & THE LAW
- PARENTAL CONTROLS
- RESOURCES
MOULDING A CYBER SMART GENERATION
Dear Parents & Teachers
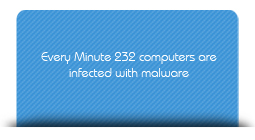
The online population is a mixed bag of the good, bad and ugly, hence it becomes equally important to monitor and supervise the activities of your ward online. Children by virtue of their nature enjoy exploring and experimenting, with the curiosity and ignorance come greater risks and need for supervision. They are easily vulnerable to online perpetuators and can even lead to hampering your personal data and pc. The better educated you are about online risks, the greater you can contribute towards the online safety of your ward. Hence it is required that parents and teachers equip themselves to mould a Cyber Smart generation. .
1. Awareness
The Internet is highly dynamic and as parents it is important that you stay updated with the developments and trends of the cyber world. Online perpetuators discover new ways of afflicting crime into the net every day. As a responsible parent it is vital that you remain aware of the various crimes as well as the tools and software to ensure safety.
2. Communication
We live in a world where children tend to spend more time on the net than with their parents. As parents it is essential that you develop a healthy communication with your ward on a daily basis. Encourage your child to share his/her online experiences. Be vigilant about the Internet environments in which your child interacts. React constructively when your child complaints of any online discomfort. Give them the assurance of being there for them no matter how bad the situation gets.
3. Clean System
Always ensure you have a security suite installed on your PC that includes antivirus, anti spyware and firewall. Make sure that they update automatically. Currently Internet Service Providers have inbuilt controls which help you monitor your child's online activity. The sites visited, the duration spent on each website etc can be tracked using these controls. Ensure the effective use of these parental controls.
4. Social networking sites & safety
Today children as young as 10 sign up for social networking sites. With such a young audience at the receiving end, parents should be cautious regarding the way the child conducts himself online. Involve positively in the online activities of your child. All social networking sites come with privacy setting preference. Collectively decide and discuss the most suited option. Teach your child about the threats of disclosing sensitive information. Ensure that your child does not go out for a face to face meeting with online acquaintances.
5. Explain the hazards
For most children the Internet is a fantasy world and hence they tend to overlook their own security and risks. Teach them to distinguish between the right and wrong on the net. Instruct them not to share photos and pictures with online acquaintances. Instruct them not to post any information that is embarrassing or hurtful to the people he/she is addressing. Inculcate the habit of respecting the views and ideas of other people online.
6. Support
In case your child complaints of any unusual activity online deal with it constructively and positively. Assure them of your constant help and support. Work with them on strategies in case they come across online predators such as cyber bullies, paedophiles or any online disturbances.
AN INSIGHT INTO REALITY
Most parents take pride in the fact that their ward is computer literate. But do you think your ward is literate and aware about the potential risks of inappropriate usage of the Internet?? Above all are you fully aware of what your child is doing on the Internet??Are you equipped enough to guide them??
Here is an insight into some of the most used Internet commodities and their fact file.
1. Social networking sites


Impact
Excessive use of social networking sites can lead to addiction which is very commonly seen among children.
This in turn leads to lack of focus in studies and deviation from their main stream goals.
2. Chat rooms
They are tools which enable chatting and exchange of photos and videos. Chat rooms can have people of different ages, different types and different kinds.
Benefits
They form cheap means of communication.
They bridge the gap created by distance and geography
Disadvantage
Cyber criminals can dupe young children by posing as friends of their age.
Paedophiles [sexually attracted to children] find this to be the easiest medium in locating their prey.
Lack of caution and awareness can lead to severe consequences.
Impact
Excessive usage without proper caution can lead to ultimate exploitation of children
3. Online gaming sites
Currently there are plenty of sites which provide with online gaming options.
Benefits
Gaming made available at finger tips
Source of entertainment for kids
Risks
Excessive gaming leads to addiction
Inappropriate and fake gaming sites can inject virus into your computer
4. Downloading music and movies
Children love downloading their favourite music and movies from the Internet. Some websites offer free download while others charge for the downloaded content
Benefits
Risks
Online Generation Gap
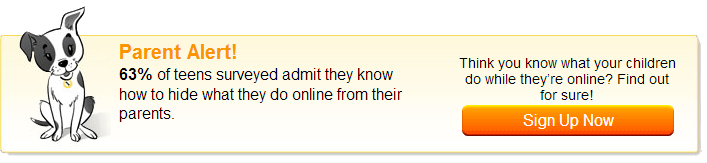
Your concern and protection as a parent necessarily need not seem the same from your child's point of view. Most of the teens hate their parents viewing their web history and entrusting them with a whole list of do's and dont's when it comes to using the net. This persistent difference in ideas and concepts gives way to an online generation gap.
CYBER BULLYING & HARASSMENT
Cyber Bullying- refers to the deliberate use of Internet for repeatedly harassing or intimidating an individual or group of individuals. Cyber bullying has been defined by The National Crime Prevention Council as follows "When the Internet, cell phones or other devices are used to send or post text or images intended to hurt or embarrass another person." Cyber Bullying is one crime which can be extensively seen among teenagers and young adults.
Identifying cyber bullying
Cyber bullying is propagated by two methods namely:
Protection against Cyber Bullying
1. Limit personal data
Explain to your child the importance of limiting personal and sensitive information. This reduces the chance of being bullied and prevents impersonation to a large extent.
2. Avoid sharp reaction
Bullies largely thrive on the reactions of their victim. Do not instigate them with hostile behaviour or rude replies as this shall lead to the escalation of the situation. Instruct your child to ignore the bully. Currently all social networking sites have an inbuilt option for blocking people. If your child is a victim of cyber bullying via mail consider changing the email id. In case the bullying still persist sort to strict legal action.
3. Record the statements
In case your child confronts with a cyber bully record and document all the messages received with date and time. This can prove extremely handy in case you plan to take it up legally.
4. Reporting cyber bully
If you or your child is being persistently cyber bullied take up the case with local authorities. Every country has its own legal provision to deal with cyber crimes.
WARNING SIGNS OF A CYBER VICTIM
The below given signs are indications that your child/student just might be victimised.
1. Spending long hours on the Internet especially during nights
2. A general reluctance towards family and friends
3. Constant calls from strangers
INTERNET SAFETY TIPS FOR PARENTS
1. Place the computer in a common area
2. Insist that they don't disclose any personal information such as address or telephone numbers online.
3. Supervise kids when they work online for long hours at home
4. Tell your child not to share their passwords even with friends.
5. Discuss the consequence of posting sensitive information online.
6. Enable filters that are inbuilt in web browsers and ensure the efficient use of parental controls
7. In case your child complains of any uncomfortable online exchange, take it seriously
8. Talk to your child about Internet safety today. It is never too late.
SOFTWARE PIRACY & THE LAW
Software piracy refers to the unauthorized copy or use of copyrighted software. It is simply the illegitimate possession of somebody else’s property.
RISKS
Software piracy is a crime be it copying or using such software. The firm whose software is being copied can sue the user by a fortune
Though pirated software comes cheap it comes with the ultimate hallmark of being malicious. With the source being unknown there is no authority or body against whom you could complain rather your image gets tarnished as it is a punishable offence
PREVENTION
The children of cyber era are true Internet experts in their own capacity. Downloading comes easy to them rather than purchasing the legitimate software. Create awareness in your child regarding software piracy and it’s risks. Encourage the use of authentic software among children. Be a role model to them by installing only authentic software in your pc/laptop.
PARENTAL CONTROLS
The Internet is a very wonderful way of enhancing your child’s knowledge. On the other hand today the Internet is proving to be the breeding ground of cyber menace with young children being victimized. Such malice can be easily avoided by using parental controls effectively. Parental controls refer to the various software and tools that help you monitor your child’s online activity.
Here are a couple of essential aspects of parental controls
1. Auto Alert. Can be programmed to send automatic e-mail alerts triggered by specific events, such as viewing an inappropriate web
page or IM message.
2. Block Private Information. Can be configured to blocks the transmission of private information such as name, phone number, etc. via IM and e-mail.
3. Contact Management. Control over who can contact children via IM, E-mail, and social networks.
4. E-mail Block and Monitor. Ability to block or monitor e-mail for a user through an e-mail program such as Outlook, as well as web based e-mail such as Hotmail.
5. Game Rating Management. Allows the enforcement of gaming ratings systems, such as ESRB on games played on a computer.
6. IM Block and Monitor. Allows the blocking or monitoring of instant Messaging programs, such as Windows Live IM, Yahoo IM, AOL, etc.
7. Multi Profile. Allows for the creation of multiple user profiles with different levels of filtering, blocking, and monitoring.
8. P2P Block. Blocks the downloading, installation and use of peer to-peer file sharing software.
9. Safe Search control. Allows for the safe search setting of popular search engines such as Bing and Google to be locked in place.
10. “Keyword” refers to the ability to block certain keywords from being entered in all search engines, rather than enforcing search engine
Settings.
11. Screen Capture. Ability to record screen captures of all Internet activity
12. Social Network Monitor. Ability to record all activity conducted on social network sites, such as uploading photos, sending e-mail, etc.
13. Time Management. Ability to limit Internet and/or computer use to preset times.
14. Web Filter List. Contains a pre-selected list of categorized websites for blocking, rather than simply the ability to block web.